Latest Facts
Airlines
Airlines
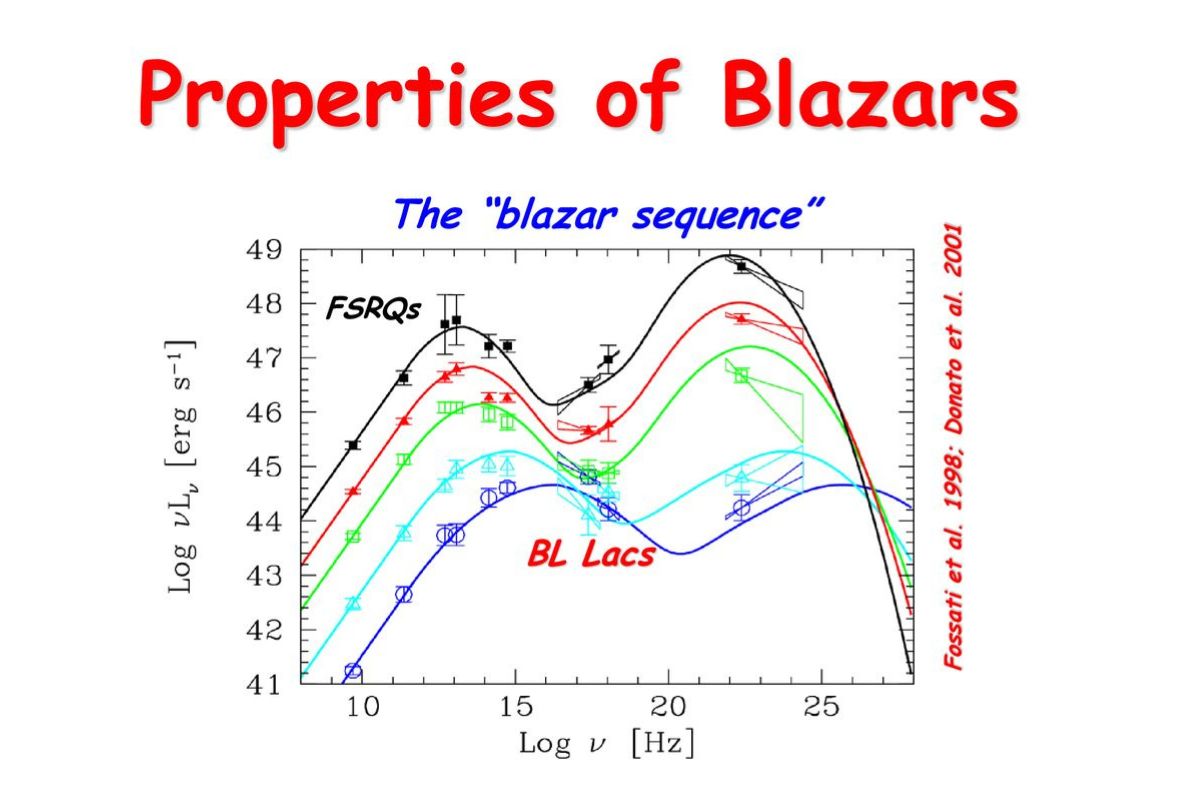
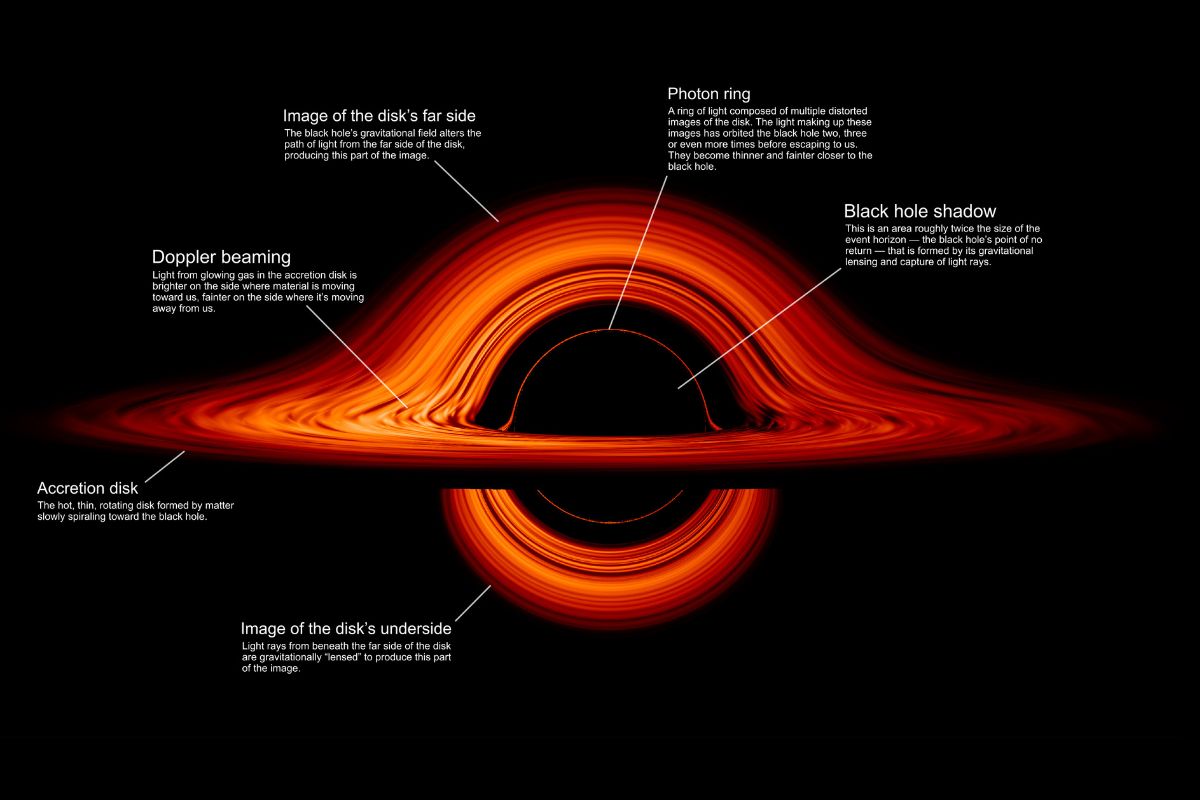
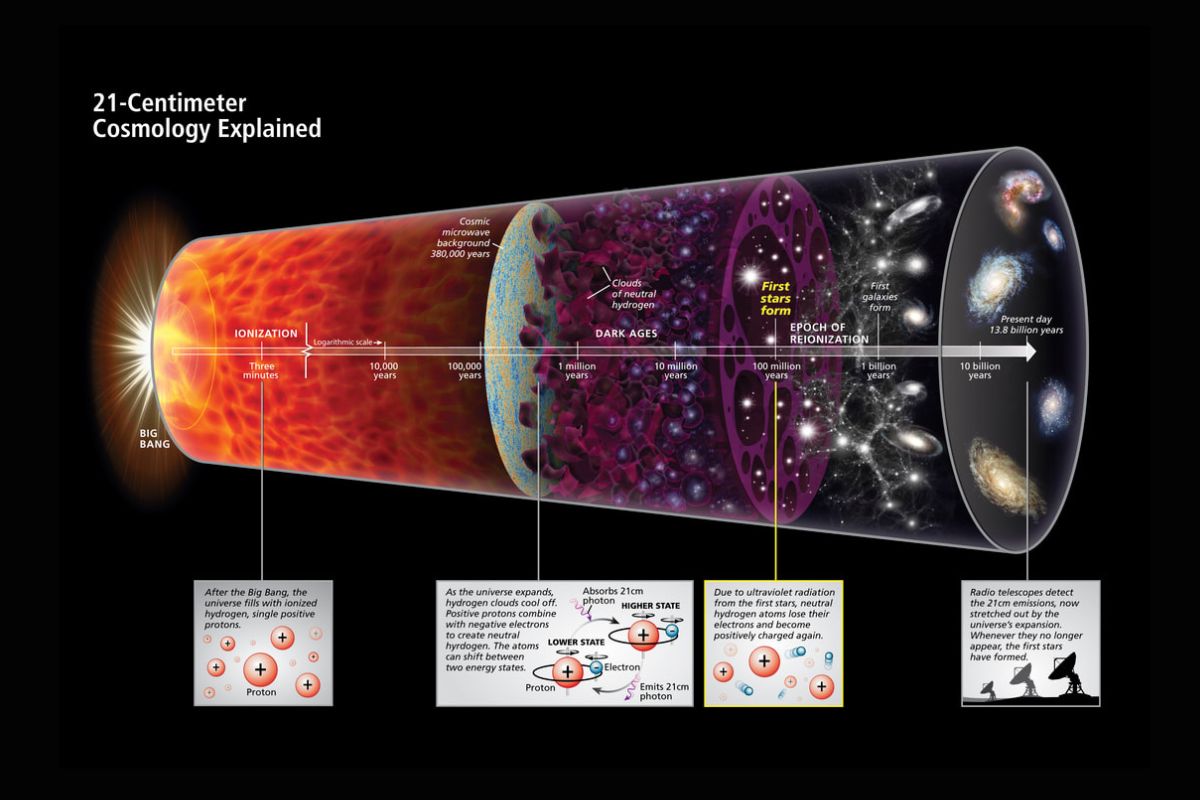
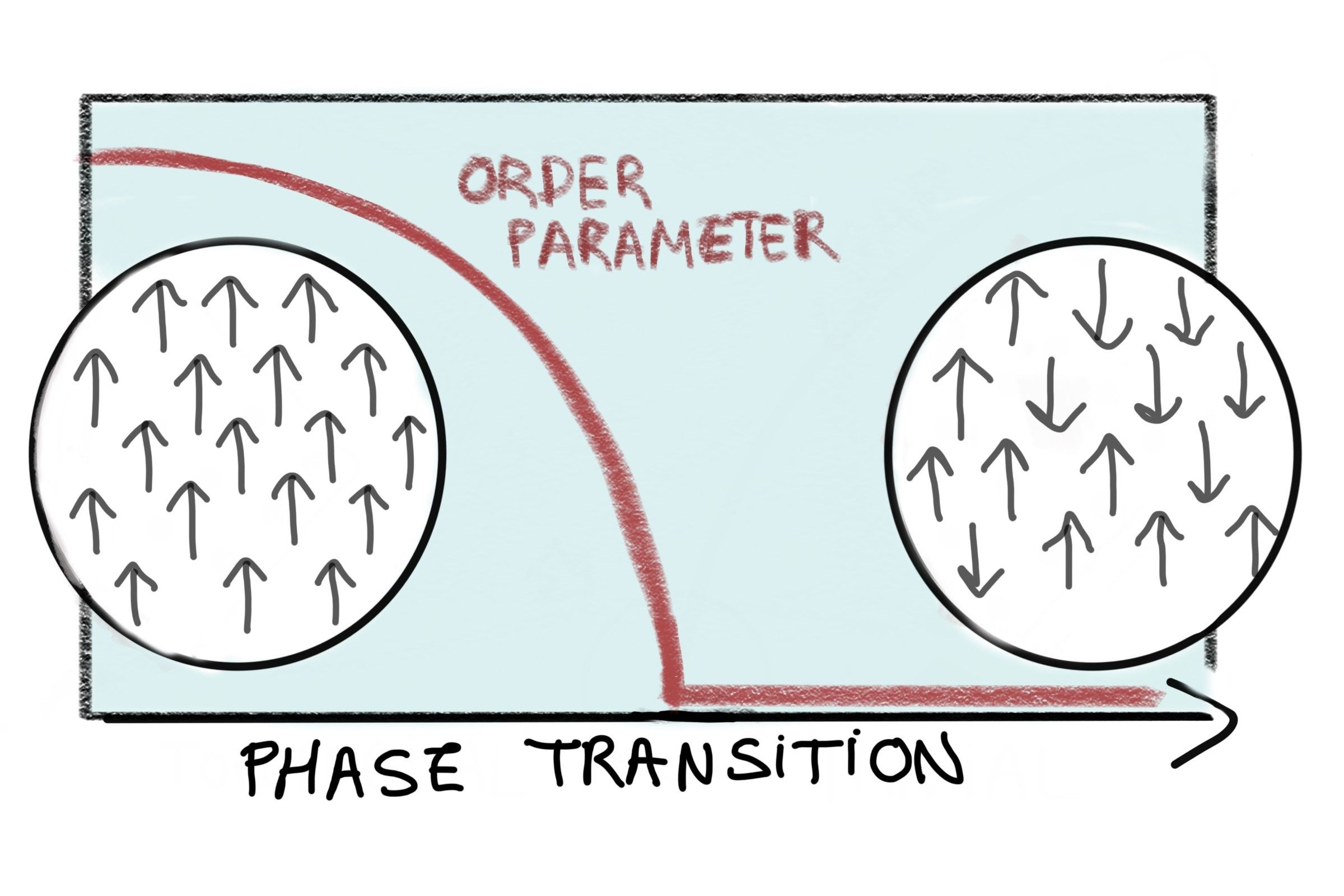
Universe
Pokemon
Universe
Airlines
Airlines
Airlines
Universe
Airlines
Airlines
Airlines
Pokemon
Airlines
Airlines
Airlines
Airlines
Airlines
Airlines
Airlines
Airlines
Airlines
Universe
Airlines
Airlines
Airlines
Airlines
Airlines
Airlines
Airlines
Airlines
Universe
Airlines
Airlines
Airlines
Airlines
Airlines
Popular Facts

Top 20 Mexican Foods
Craving a culinary adventure that’ll make your taste buds dance? Mexican cuisine offers a vibrant tapestry of flavors, textures, and aromas that can transport you straight to the heart of […]